WEB-APPLICATION TESTING
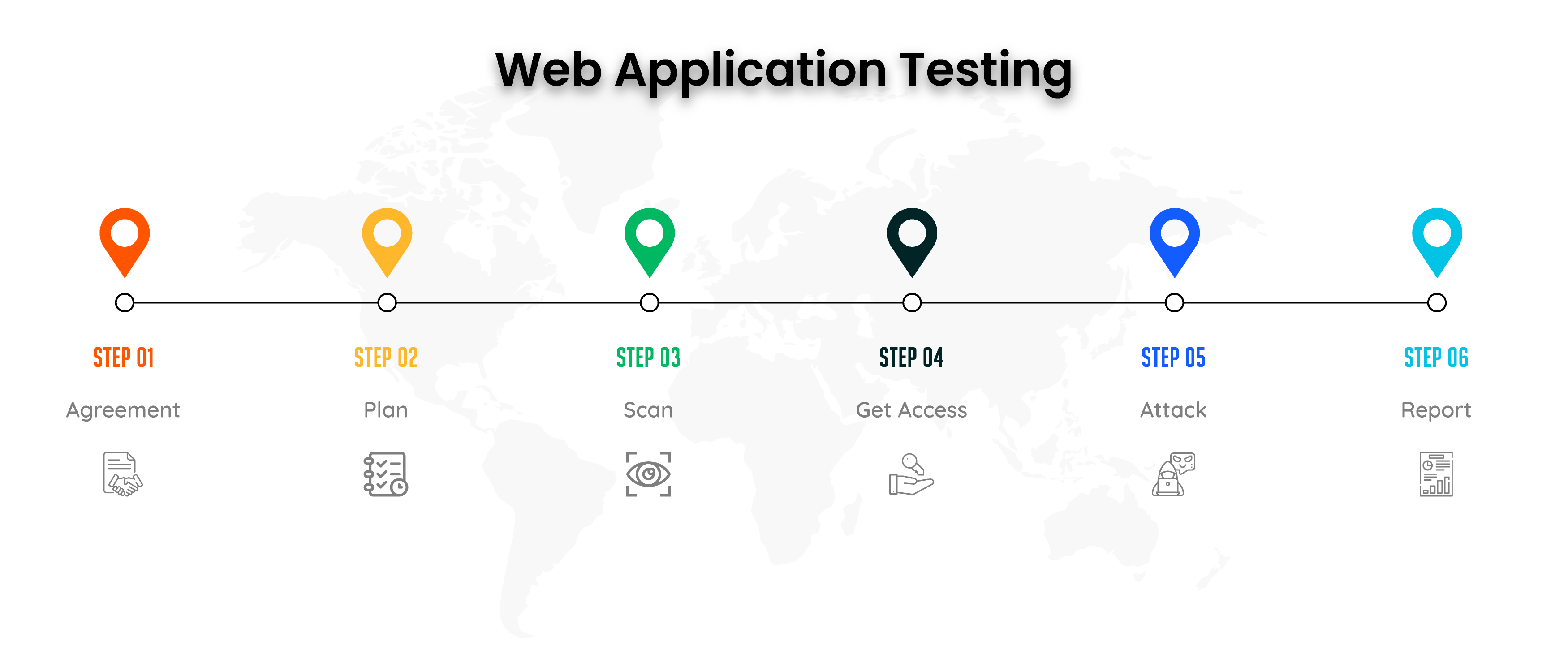
Web Application Testing Workflow
Pre-Engagement
Our team will conduct a functional analysis of the application, user functions, business logic, and application structure. When code analysis is used, the entire application's codebase is evaluated. This procedure assists our security experts in identifying possible attack vectors used by hackers.
Threat Modelling
The following stage of an application security test is to build an application's threat profile. Our threat models are developed following your business's requirements for application security. This results in tailored security testing that goes beyond standard web application penetration testing.
Security Assessment Plan
The web application security assessment plan details the research strategy used to conduct security checks. The test plan would cover possible exploit methods that could jeopardise user rights, business logic, or transactions or reveal sensitive data.
Application Security Assessment
Crypticonic Security conducts the application security test plan during this time. Unlike software testing, however, the performance of a security test is not always as predefined, and therefore the plan must be updated continuously as the situation develops.Crypticonic Security experts pivot the strategy to simulate actual hackers by using their extensive expertise. This potentially results in the discovery of additional vulnerabilities that may result in findings of critical bugs..
Reporting Vulnerablity
Once the assessment is complete, a detailed written report outlinin`g each observed and or exploited vulnerabilities, along with the root cause analysis and categorisation along with mitigation and confirmatory re-test certificate if the need arrives.